Please notice: This article is more than 3 years old
Content, Source code or links may no longer be correct in the meantime.
February 17, 2021 | 08:00Reading-Time: ca. 3 Min
Leak Checker Comparison
There is an uneasy feeling when reading reports of major hacks and data leaks. Am I exposed is the main question. Leak checkers promise to provide answers. The Hasso Plattner Institute (HPI) in Potsdam runs a well-known plattform1, another from the University of Bonn2 is slightly less popular. Both share the same functional principle: Get an email, compare it with a database full of leaks, send back the answer. The details are where the differences lie, and unfortunately they are not comfortable.
Integration of Google resources
The HPI disqualifies itself by including externally linked Javascript resources from ajax.googleapis.com. The resource in question is an outdated JQuery library version 1.11.0 with numerous documented vulnerabilities3. A visitor is not asked about the data transfer of his IP, browser data and the time of the retrieval to Google. There is no information provided in the privacy policy4.
However, the Bonn-based website does a better job but with other inconveniences. Modern security features remain unsupported. An HTTP Strict Transport Security (HSTS), a Content Security Policy (CSP), important HTTP headers against XSS and X-Frame attacks and the referer-suppression are missing5.
The carelessness and lack of implementation of modern internet standards in both projects is surprising.
Email-Server
The astonishment continues when observing the email infrastructure. The result emails came from the hosts mail2.hpi.uni-potsdam.de for HPI and mail.uni-bonn.de for LeakChecker.
Both mail servers work with TLS 1.0/1.1. Ciphers are not specified on the server side and allow a downgrade. Common security standards such as SPF, MTA-STS, DNSSEC or DMARC are not supported. The University of Bonn made a configuration error with the DMARC entry. The reporting email refers to a third party provider6 without the necessary permission record7.
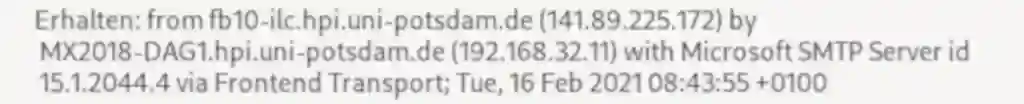
The mail server of HPI does not strip email headers and allows an insight view into the campus network of the University of Potsdam. This reveals a rotten Microsoft Exchange Server 2016 with the internal IP 192.168.32.11, which obtains my result mail from the application server and relays it. According to the server identifier 15.1.2044.4, it is lagging two patch versions behind and is at the level of 16.06.20208.
Results
The results are sent back via email within minutes after submission. Abuse is prevented by strong rate limits. Only one email per week can be requested via the University of Bonn. The HPI replies are signed with an PGP cert. From practical considerations, this does not seem to make sense. The identity of the sender cannot be verified by a recipient and generates unnecessary warning and error messages in the email programs. Trusting an untrusted email in this sensitive matter would be beyond the ability of the average end user unfamiliar with PGP.
The results are displayed in tabular form in both emails. On the positive side, the Leak Checker from the University of Bonn displays the first and last letters of a password. The HPI tool in contrast was better in identifying the affected services.
Bottomline
Both tools tell more about their operators than the operators would like them to. This does not present the HPI favourably. In comparison, the Bonn-based tools perform better and present a more modern design. If these tools are intended to promote security and data protection, I am quite disappointed. Furthermore, it is a pity that the web frontends and the database queries cannot be reviewed in the source code. That might have provided more transparency and increased trust.
The HPI tool should only be used with a browser in which 3rd party queries are automatically blocked. In terms of the results, both tools complement each other and give a good overview and introduction to managing access with the help of a password manager when used in combination.
https://www.cvedetails.com/product/11031/Jquery-Jquery.html?vendor_id=6538 ↩︎
https://webbkoll.dataskydd.net/de/results?url=leakchecker.uni-bonn.de ↩︎
look RFC 7489, Sec 7.1, https://tools.ietf.org/html/rfc7489 ↩︎
https://docs.microsoft.com/en-us/exchange/new-features/build-numbers-and-release-dates ↩︎