Please notice: This article is more than 3 years old
Content, Source code or links may no longer be correct in the meantime.
August 23, 2020 | 15:04Reading-Time: ca. 12 Min
Working in your Homeoffice - Part I
Home Office Workstations - Introduction
How to integrate a corporate home office securely? And preferably also in a cost-effective, transparent and sustainable way! Some people might have been busy on this question due to Corona lockdown.
As an external contractor, I used to stand at the sideline more than once and looked into the big arena of swarm idiocy1 and stupidity2.
With this picture in mind, I’m launching a new blog series describing what I think a home office workplace for small and medium-sized businesses should look like. As always: No solution fits every use case universally. Your mileage may vary and of course the remark: I am buyable for exactly such challanges.
Starting off with the basics of what is considered as standard in information security. You will find orientation in the VdS 10000 Information Security Management System for small and medium-sized businesses3. With an excursion into the world of hacking, I will show why transplanting a Windows-based workstation from the internal domain into foreign networks and connecting it with VPN is a dodgy idea. At the end of the first part I show the concept of a portable branch network.
The second part of this blog series deals with terminalservers. Primarily I want to show how cost-efficiently and quickly all workstations of a business can be transformed into home office workstations. Using multi-factor authentication, TLS encryption, central management and above all without any additional client software blackbox installations. And since the starting point for phasing out any proprietary software is going through terminalservers, I also show how straightforward, inexpensive and quickly a Debian Linux terminalserver with a complete office environment can be set up.
In the third and last part we evaluate the risks and consequences. This might not sound very exciting at this point, considering the wealth of topics covered in the previous parts. It also might sounds quite unimportant. However, it is not. Top management always needs facts easily to understand and an administrator needs clear guidelines and policies.
As always, constructive criticism, comments and discussion are welcome.
Now what about Infomation Security Management?
Basically, information security guidelines for home office workplaces MUST be developed, starting and committed by the company’s top management4. Top management must not only approve the guidelines but also ensure that every employee understands them. This implies an appropriateness that fits the respective working situation. Nobody will be able to understand or execute instructions like “You must encrypt files AES 2565”.
Without proper training and awareness, no one should be assigned to a home office and left alone. Of course, nobody will admit by himself to have shortfalls in the use of his/her day-to-day tools, but that’ s another issue.
Clear performance or abortion criteria and, if necessary, the option of imposing sanctions should be available. Not everyone is able to work from his/her home office. That’s a fact and nothing to worry about. It only turns into a problem if it is not taken into consideration before.
Homeoffice workplaces are understood as mobile IT systems that require special security measures6 beyond a basic protection7 to protect against threats such as theft, unauthorized access or network transitions (home network, mobile network). Simply pulling a computer out of the internal network using a VPN does not meet these requirements. Additional regulations for backups8 and multi-factor authentication9 for remote access must be found.
If a dial-up via VPN is made, meaning linking and connecting to the organization’s network, then this has to secured additionally on network level10. IDS/IPS systems are mentioned and recommended explicitly. And usually when it comes to a segmented corporate network, we rarely speak of only one system, there should be multiple ones, at least one in each logical entity or location. Against the general recommendations of many retailers, who tend to lead customers straight into digital dependency with expensive subscription plans from Fortinet, Sophos and others on extra hardware, I’m talking about open source IDS/IPS systems, which are neither expensive nor complex and can be operated on standard hardware.
Last but not least: When it comes to portable IT devices and increasing video and screen sharing activities, the question arises more than ever before: What to do if the device or credentials have been lost? Who informs whom, where should accounts be blocked immediately? 11. Something I see frequently: Copy & Paste while screen sharing or remote controlled. I wonder if people are familiar with the fact that clipboard content is shared with the participants aswell only depending what software is used? I have a nice little tool that polls the content from the clipboard into a text file every second. Quite nasty isn’t it?
Kudos to all who implemented information security guidelines before Corona and who were able to apply them without any arguments and especially who remained resistant to the bullshitters talking about “Exceptional times require exceptional measures”. However, those who do not have an information security management and neither used the lockdown as boost to establish one, will most likely be among those who are currently messing up their digitization. The question is not “if” but “when” everything will go to shit.
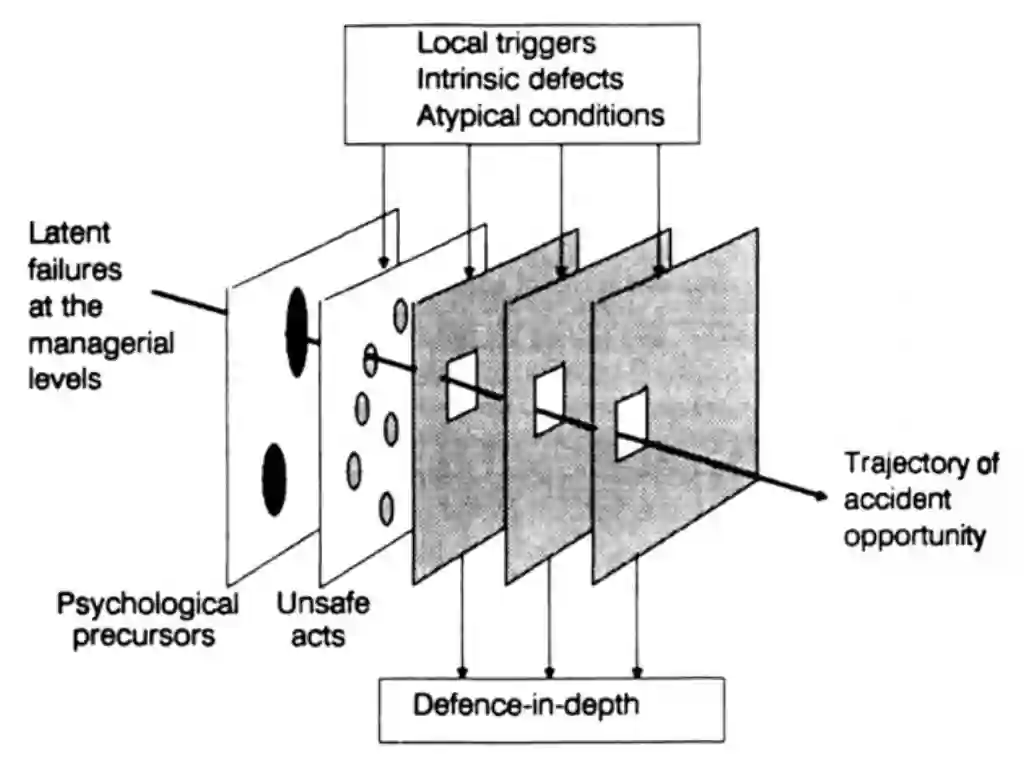
As a recreational pilot, I like to draw comparisons with aviation. Risks and threats have to be balanced and mastered when dealing with complex technology. If you don’t plan your flight in advance, if you don’t catch up with the weather forecast, if you do not use NOTAMs and finally if you never learned how to use checklists and consider them as a escape from a “trajectory of accident opportunity”12, then you might be able to fly around your home airfield for many years. However, in the first dicey situation beyond your comfortzone you’re surely doomed.
An evil aviation proverb says: “The air cleans itself”. Unfortunately, I am not aware of any comparable proverb in information security.
Internal Windows computer with external VPN dial-in
The usual home office workstation consists of a Windows notebook, managed by the company’s internal Active Directory (AD) and equipped with VPN access for dial-up via the home WLAN. This configuration presents various challenges:
Private networks do not have an adequate level of protection. The bandwidth ranges from outdated or incorrectly configured routers, existing malware on other computers to unknown network configuration flaws.
Computers operated in this way are “dual homed”13, in other words connected to several interfaces in different networks, usually to the private WLAN and the corporate network.
The security of the entire network depends on the security of the weakest member. Any dual homed device becomes a prime target for attacks, as it is usually more accessible and less protected than the more hardened and controlled network gateway.
Excursus: WLAN hacking
At this point a short journey into the world of pentesting and WLAN hacking. Apart from the know-how, only a little bit of crafting skills are needed to create a WLAN sniffer. I’m quite lazy and using a ready-to-hack Pineapple14 which gives me the advantage of being able to automate many functions and get beautiful summaries.
The procedure is always the same:
- Determining the target device from the number of radio devices
- Record and examine all WLAN/MAC addresses requested by this device
- Spoofing a WLAN known to the device with a RogueAP15
- Deauth attack16 to disconnect and reconnect with your own RogueAP
Please note this disclaimer: Deauth attacks represent a criminal offence as a hacker attack and in addition are prohibited by the German Federal Regulatory Authorities17. These may only be carried out in the own network and equipment and under laboratory conditions with weak transmitting levels. It is smarter to set up a RogueAP in unexpected places with the SSID/MAC of the home network and just wait until your notebook connects automatically.
Interestingly an ideal place is the office within the company, exactly when the notebook is plugged into the corporated network by a wired connection but keeping the WLAN activated. That’s where Windows is limited by the fact, that it doesn’t know anything about network profiles or up/down rules. It simply connects to the known home network without prompting the user.
Using such a well positioned RogueAP (ironically housed in a small arms case) I can run it for some days. As soon as the target computer is on the hook, I receive an email notification as a new man-in-the-middle18. This was the more complex part.

Via the computer into the corporate network
In order to takeover a computer, local administration rights are required. Unfortunately, these are still assigned far too carelessly. It doesn’t have to be due ancient software. Modern, colourful and shiny gaming mice or keyboards 19 might indicate even from afar that someone is possibly working with local admin rights. As a rule of thumb, these are usually power users or those who are considered most advanced, trendy or skilled.
It really doesn’t get complicated when you have to obtain local admin rights. This usually requires a vulnerability for privilege escalation20. Careless Adminstrators are also welcome when passwords are stored in plaintext all over the system. In my experience, the possibilities on managed domain computers are far better than on private ones. They don’t have service accounts, logon- or update-scripts, remote backups, time-recording, monitoring or inventory software.
There are enough YouTube clips21 and Internet tutorials22 which are much better at explaining how to take over a Windows computer. Not every tool fits the target at the first attempt.
As a matter of fact: Once on a Windows workstation, which is simultaneously a domain member of a corporate network, and the match is over. Quite comparable to a 5:1 in the 85th minute in an international soccer match: Obtain debugging privileges, execute mimikatz23, read the passwords in plain text, job done!
One small piece of comfort left: The game is not quite over yet. Bonus miles are only available when the Kerberos TGT User24 and the “golden ticket” are obtained. That’s the final blow to any AD infrastructure. From this point on, only a new installation of all servers and workstations would help.
Unfortunately, this is exactly what stakeholders do over and over and over again in the hope that something will change. Vaas Montenegro sends his greetings25. Another fun fact: The tools mimikatz and kekeo are actually only “side-projects” of Benjamin Delphy, the french developer behind. He originally just wanted to learn some C and experience Microsoft Windows26.
Back to our homeoffice computer. Nobody trusts Microsoft Office documents in email attachments anymore. But the allegedly home network all the more. SMB network shares and printers are willingly shared, and corporate admins assume they are in a trustworthy environment for their corporate VPN. A single line of netsh is enough for a network bridge27.
Safeguard measures
To me Windows as operating system is structurally broken and can only be operated safely in isolation without any direct internet access. This would also be the ultimate answer to all questions regarding data protection laws. Of course, this radicalism is rarely practicable and the situation is not as hopeless as it may seem now.
An application whitelisting, for instance, has been a part of every Windows since Windows XP, regardless of whether you are a domain member or not. Managed and rolled out within an AD, it is called Software Restriction Policy28. This would stop the execution of mimikatz and other tools, for example.
Another possibility would be to completely avoid WLAN and to set up a home office only using wired and controlled end points.
Concept of a mobile location
I got the idea from a construction sector client’s scenario. A on-site network with three segments was required. In addition to the client’s own supervisors, external contractors were also to be given access to the internet, of course wirelessly. As a matter of course besides POE webcams common printers/scanners including SMB network shares for scanned documents should be added. All these things with enough potential to cause severe security nightmares in an environment that can at best be considered as “rough”. Another contributing factor for increased general uncomfortability is the effect of metal construction containers and all kinds of heavy metal equipment on cellular and WLAN signals29. A robust, flexible and at the same time easy to operate solution (“the red cable here, the green cable there”) had to be found. The construction site box was born:

A complete network consisting of LTE-Fritzbox, 8-Port POE Switch, an ipfire.org30 Firewall and some more extras. Securely stored in a lockable 10", 6U metal chassis. The remote peer in the company also consists of an ipfire and enables fine-grained access to selected resources with firewall and routing rules. Two IDS/IPS31 run independently on both sides with SNORT rules reporting and blocking suspicious pings, network or port scans.
My own homeoffice
I have such a box in my own home office. One nice detail: The 10" network chassis made by the Sauerland-based manufacturer fits perfectly into an IKEA KALLAX/EXPEDIT shelf.

Apart from the previously presented construction site box, I use different gadgets such as a managed switch and a higher quality firewall with 4x Gigabit interfaces. But the principle remains the same: Only the secure, hard-wired green segment is connected to my office via VPN. The radios of the connected devices remain switched off.
With a switch, socket rail and insertable shelves, such a small enclosure is priced around 150-200,- EUR. A barebone for the ipfire.org is also available in the same price range. On top of that there is also time for planning, assembly and installation. Put all this together, it’s just a fraction of the costs and damage that may occur in the worst-case scenario.
The biggest benefit: As long as only standard hardware and free open source software is used, you remain completely independent from the price and product policy of the major tech companies with their own concepts of product life cycles, IT security and data protection.
This is what I consider as sustainable, flexible and long-term digitalization.
https://www.campus.de/e-books/wirtschaft-gesellschaft/wirtschaft/schwarmdumm-9794.html ↩︎
https://www.campus.de/buecher-campus-verlag/wirtschaft-gesellschaft/wirtschaft/flachsinn-10854.html ↩︎
VdS 10000, 6.1 and 6.4 ↩︎
https://de.wikipedia.org/wiki/Advanced_Encryption_Standard ↩︎
VdS 10000, 10.4 “Zusätzliche Maßnahmen für mobile IT-Systeme” ↩︎
VdS 10000, 10.3 “Basisschutz von IT Systemen” ↩︎
VdS 10000, 16.5.4 “Datensicherung mobiler IT-Systeme” ↩︎
VdS 10000, 11.4.3 “Fernzugang” ↩︎
VdS 10000, 11.4.4 “Netzwerkkopplung” ↩︎
VdS 10000, 10.4.3 “Verlust” ↩︎
James Reason, “Human Error”, 20th printing 2009, Cambridge University Press, page 208 ↩︎
https://www.elektronik-kompendium.de/sites/net/2109171.htm ↩︎
https://www.golem.de/news/bundesnetzagentur-nutzung-von-deauthern-ist-nicht-zulaessig-2001-145911.html ↩︎
https://insider.razer.com/index.php?threads/every-time-i-start-cortex-it-asks-for-admin-permissions.54669/ ↩︎
🚫 https://www.christophertruncer.com/golden-ticket-generation/ ↩︎
https://www.wired.com/story/how-mimikatz-became-go-to-hacker-tool/ ↩︎
https://docs.microsoft.com/en-us/windows-server/networking/technologies/netsh/netsh ↩︎
https://docs.microsoft.com/de-de/windows/security/threat-protection/windows-defender-application-control/applocker/using-software-restriction-policies-and-applocker-policies ↩︎